If you are in this sector and covered by this legislation, it's critical that you take steps to comply.
if you haven't already. Not simply because of the regulatory demands, but ultimately non-compliance could stop you from collaborating with other entities or hinder business progress.

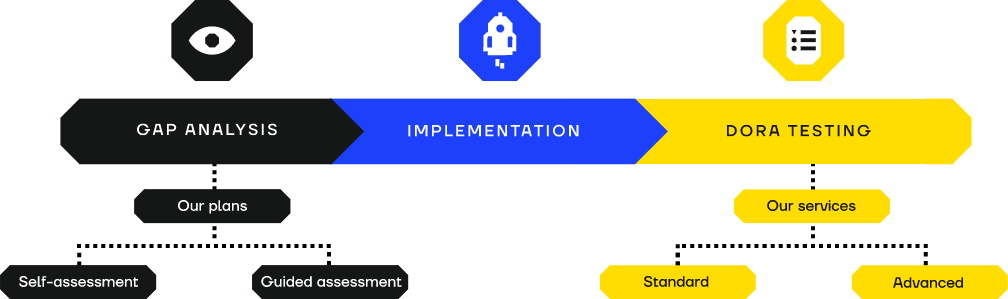
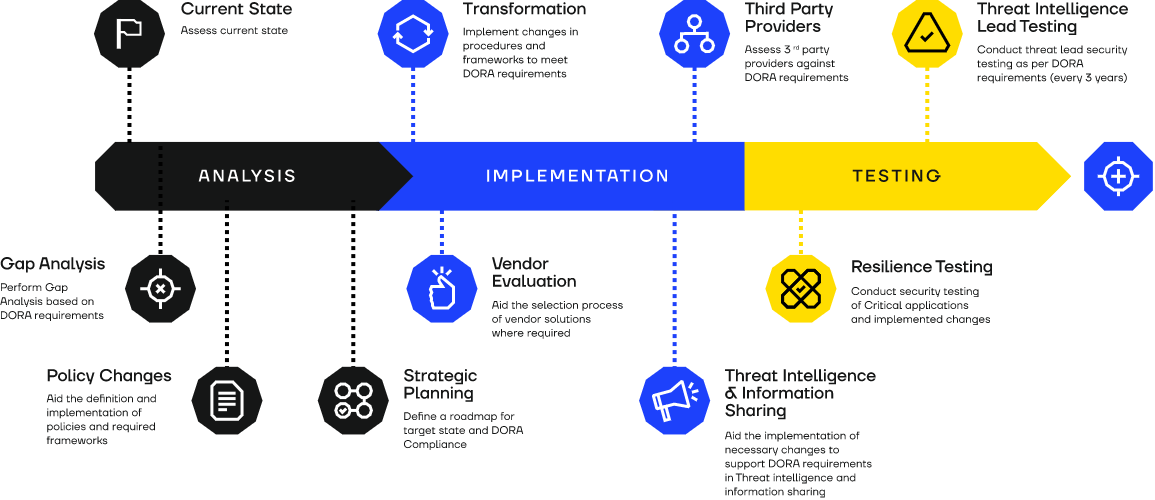
Here at SECFORCE, we have the capability to help you comply with all areas of the existing regulations;
And go further to ensure you reach the cyber resilience and maturity level that serves your business as well as the regulations.