Some time ago we were performing an internal penetration test an we identified a Canon iR C2880 printer within the IP range in the scope of testing. Printers is the kind of device that a penetration tester tend to dismiss as they don’t look very attractive from the attacker’s perspective.
It is a fact that printers are usually installed with all the settings by default. This includes having the default administration password (if any), default administrative interfaces enabled, default services running, default SNMP community string, etc.
It is interesting to note that some printers run an anonymous FTP server that users (and processes) can use to print documents. A user can upload a document to the FTP server running on the printer and it will be printed. Things get worse when you discover that the FTP server supports the PORT command.
The PORT command is sent by the FTP client to establish a secondary channel for data to travel over. This command can be abused by attacker to network scan other hosts on your network, as shown in the next diagram:
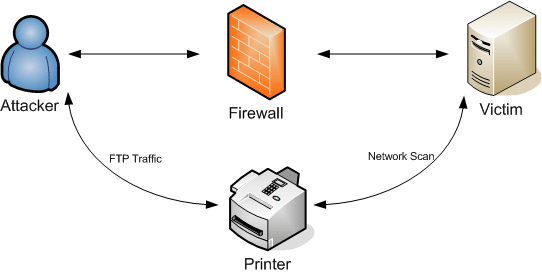
Why an attacker would want to do that? Well, there might be several reasons:
- The target host is not reachable from the network segment the attacker is connected but it is from the printer.
- The target host is reachable but there is a firewall filtering some of the traffic whereas the printer has full connectivity to it.
- The attacker wants to remain stealth and conduct the scans only using FTP connections to the printer without triggering any alarm from potential IDS systems.
This is an example of how the sniffed network traffic would look during an FTP bounce scan:
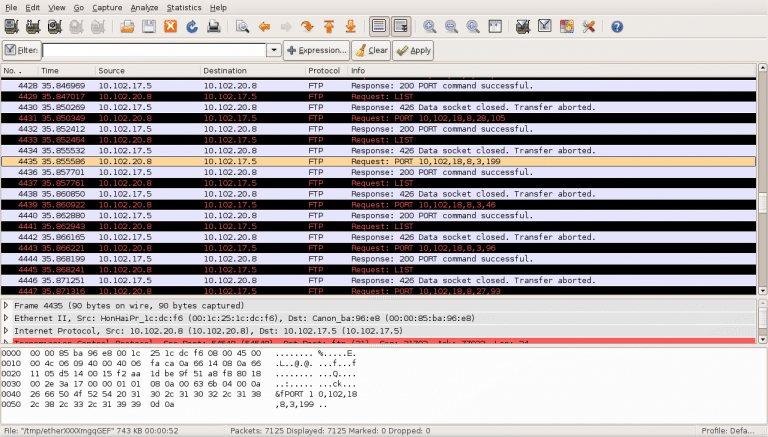
The network traffic screenshot shows that the attacker is using the printer as a bounce host and the only traffic exchanged is FTP based.
As you can see, IT security and penetration testing is about identifying every issue in your infrastructure and exploiting the weakest link.