AWS is becoming one of the most prevalent cloud solutions in the world and, as a result, reviewing the configuration of AWS infrastructure is emerging as a necessary and regular assurance exercise for most organisations in the current security landscape.
The AWS configuration in itself entails a multitude of instances, containers, users, network groups, ACLs, etc, and therefore, the process of assessing them against best practice standards often becomes tedious and time-consuming.
AWSome CIS Checker is a tool which was conceptualised to solve these problems by automating the whole process of checking AWS configurations in accordance with one of the most widely used industry best practice guides: the CIS Benchmarks.
Based on Boto3, an AWS SDK for Python, AWSome CIS Checker uses the set of credentials provided on a local AWS Client configuration to verify if the elements of a certain configuration are compliant with CIS Benchmarks (currently v1.3.0). This covers all the basic checks but also allows for a “deeper” inspection of the configuration by investigating more obscure options which could facilitate further attacks vectors.
In addition, and here is where AWSome CIS Checker provides the most value, rather than generating random unmatched CIS checks as output, the tool also provides smart suggestions about issues by grouping them together into a comprehensive list (Storage, Logging, etc.) of security problems within the environment.
AWSome CIS Checker is dependant on some Python3 packages that can be easily installed by executing the following:
pip3 install -r requirements.txt
After all requirements have been satisfied, it supports multiple running options:
- Run without parameters to use default AWS cli profile:
python aws-cis-checker.py
- Use -p or --profile to specify an AWS cli profile:
python aws-cis-checker.py' -p <profile>
- Use --cis to get a detailed list of CIS Benchmark v1.3.0 checks. This option will return an exhaustive list of completed CIS Benchmark controls, showing for each one a status of “passed/failed”
python aws-cis-checker.py --cis

- Use --suggest to get suggestions about issue groups. This option will parse failed CIS Benchmark controls and return a list of generic issues with some details of why these issues were present in the environment
python aws-cis-checker.py --suggest
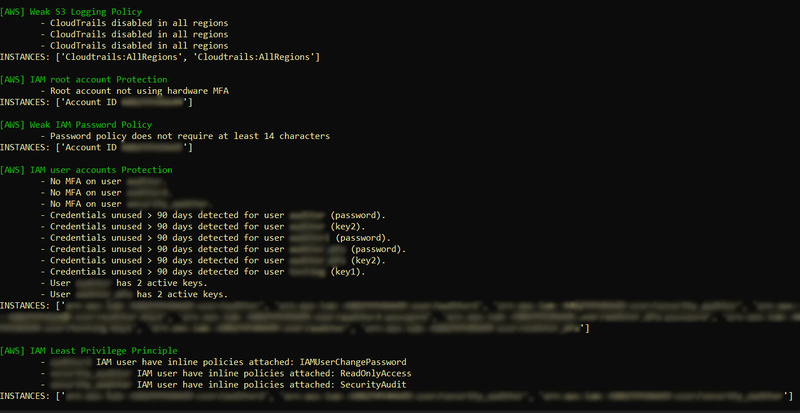
- Use --all to get both --suggest and --cis
python aws-cis-checker.py --all
You can download this new tool at: SECFORCE's Github repository