Overview:
Fortinet delivers a comprehensive portfolio of security gateways and complementary products. FortiGate platforms integrate the FortiOS operating system with FortiASIC processors and the latest-generation CPUs to provide comprehensive, high-performance security. By using a specially crafted URL in an HTTP request, it is possible to achieve an XSS attack, potentially giving access to confidential information, such as session cookies.
Description:
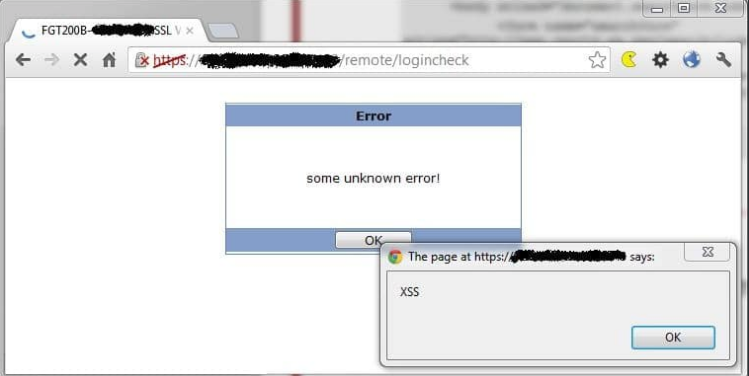
Fortinet FortiOS contains a flaw that allows a non-persistent cross-site scripting (XSS) attack. The input passed to a redir parameter at http://x.x.x.x/remote/logincheck is not properly sanitized. It is possible to inject the redir parameter in a POST request as a data parameter or trough a GET request as a URL parameter. This may allow an attacker to execute arbitrary script code in a user’s browser.
As this range of products are used for SSL VPN authentication, this issue can be exploited to mount an attack and potentially gain unauthorised access to the target internal network.
Affected Products:
Found and tested on: SSLVPN-FGT200B Remote Access Web Portal, but its known not to be the only one affected.
Proof of Concept: