Clients sometimes come to us looking for penetration testing only to discover that they really need red teaming (and vice versa).
In this article, we want to clear up the different use cases for red teaming versus penetration testing by featuring our team's insights and advice about choosing between a penetration test and a red teaming exercise.
The “Too long; didn't read” (TL;DR) version of understanding red team versus pen testing is:
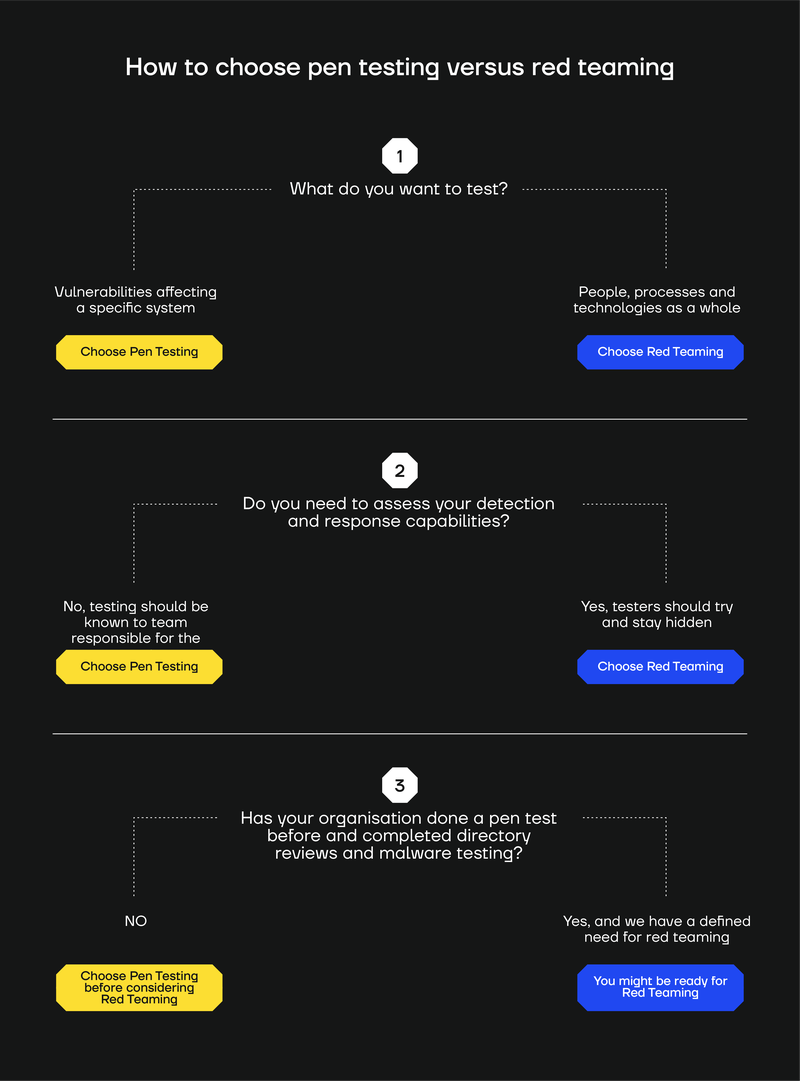
- Testing one technology/function (e.g., web/mobile application, internal network subnet, perimeter firewall) thoroughly? Choose pen testing.
- Testing your overall security posture (technologies, processes, and people) and how your organisation would perform against realistic, sophisticated attacks? Go with red teaming.
The rest of this article is a detailed guide to understanding pen testing versus red teaming use cases based on insights from SECFORCE’s offensive security team.
We also tell you about testing triggers and the maturity level you need to get the best value out of each testing type.
When to Choose Pen Testing
To test a building's security, a pen tester would check the condition of the windows and doors, looking for known weak points, as you look over their shoulder. The test would have a specific scope, and the tester would make no effort to stay hidden.
In your IT environment, you should choose a pen test to thoroughly test the security of a single asset, for example, a website, a cloud platform, or a group of IP addresses.
Penetration testing is a great fit for the following:
- Testing web/mobile applications like online banking applications before they go online and are used by customers.
- Assessing changes to control configurations, such as new firewall rules.
- Auditing controls in specific environments through laptop reviews, build reviews, and reviewing the configuration of a system, such as an IoT deployment.
- Uncovering exploitable vulnerabilities in externally facing systems (such as email or VPN) that employees use when working remotely.
- Finding and reporting on vulnerabilities to steer patch management.
There doesn't need to be a specific trigger for a penetration test, but some of the most common reasons why clients approach us to do pen testing include:
- Complying with regulations like PCI DSS 4.0.
- Assessing the security posture of individual systems or entire network segments after a breach or security incident has happened.
- Reviewing whether the deployment of new systems or any kind of change introduces vulnerabilities.
- Performing due diligence on the overall security posture. Testing a critical system at set intervals is a good practice because new exploitable vulnerabilities are discovered all the time. A test result from a year ago cannot guarantee that a system is still safe, as new exploits can make it easier for even low-skilled hackers to breach systems.
Pen testing works best for organisations that already do vulnerability scanning
A pen test can be performed on more or less any system environment, including networks, servers, employee devices, cloud infrastructure, applications and IoT deployments.
However, to make the most of a penetration test, an organisation ideally needs an established process for scanning for vulnerabilities, prioritising remediation and patching them.
Patch management is how companies remediate any identified issues they find during a pen test. A pentest is also a good way to validate that patch management processes are actually working and reducing risk.
A risk management framework could also prove helpful in identifying and prioritising cybersecurity risks, ensuring that penetration testing efforts are targeted effectively.
Beyond these basics, the maturity level you need for pen testing varies, but our experts say that you should, at minimum, be capable of creating a robust environment for testing purposes.
- Deploy a reliable test environment which accurately replicates the production environment. If deploying a test environment is not possible, the organisation needs to notify the testing provider of any sections which should not be targeted or any actions that can have a system-wide impact.
- Make the environment available to the testing provider. Often, IP filtering can be used to ensure that the environment is only reachable by the authorised parties.
- For white or grey box testing, provide the testers with access to all the necessary privilege levels to thoroughly test the system in scope.
Finally, it is very useful for an organisation to document and share its user journeys, network topology diagrams and data flow cases for any system being tested. This will ensure that the testing team has a better understanding of the assessed system and can conduct more efficient security testing.
When to Choose Red teaming
If we were to use the same analogy as we used above for pen testing, a red teamer would try to get into a building as quickly as possible and see how long it took someone to notice suspicious activity, call the police, and stop them.
The red team focuses not only on the doors and windows but also on any promising way of giving them access (e.g., luring a legitimate employee in the building into letting them in or disguising themselves as maintenance crew).
Red teaming has a wide scope, and red teamers do their best to stay hidden during an engagement.
Use red teaming to see how your organisation would fare against threats targeting your organisation’s technologies, processes, and people.
A red teaming exercise might start with a question like, “From x starting point, what can a cybercriminal do?”
Would a threat actor be able to compromise a payment system or other critical infrastructure, gain access to sensitive information, exfiltrate data, or even compromise the entire organisation?
By simulating certain scenarios, organisations can build resilience.
Red teaming test results can help organisations learn about exposures in their business processes and third-party dependencies.
It also allows organisations to benchmark KPIs like mean time to detection (MTTD) and fine-tune detections and response processes to make improvements.
Compared to penetration testing, red teaming is more fluid in scope (testing parameters often change based on what happens during a test), communication-heavy (including daily updates) and potentially risky if inadequate risk management measures are taken or communications are sub-optimal.
Generally speaking, red teaming is a more costly engagement than pen testing and tends to happen due to trigger events such as the following:
- Need to comply with regulations like the Digital Operational Resilience Act (DORA), CBEST/TBEST, and TIBER-EU.
- Desire to assess detection and response capabilities or the organisation’s ability to kick out an attacker, i.e., prove your security posture’s effect.
- Need to test new security controls and configurations put in place after a breach or compromise happened.
Red teaming is for mature security programs
If you don't already do pentesting, then red teaming probably won’t deliver much value.
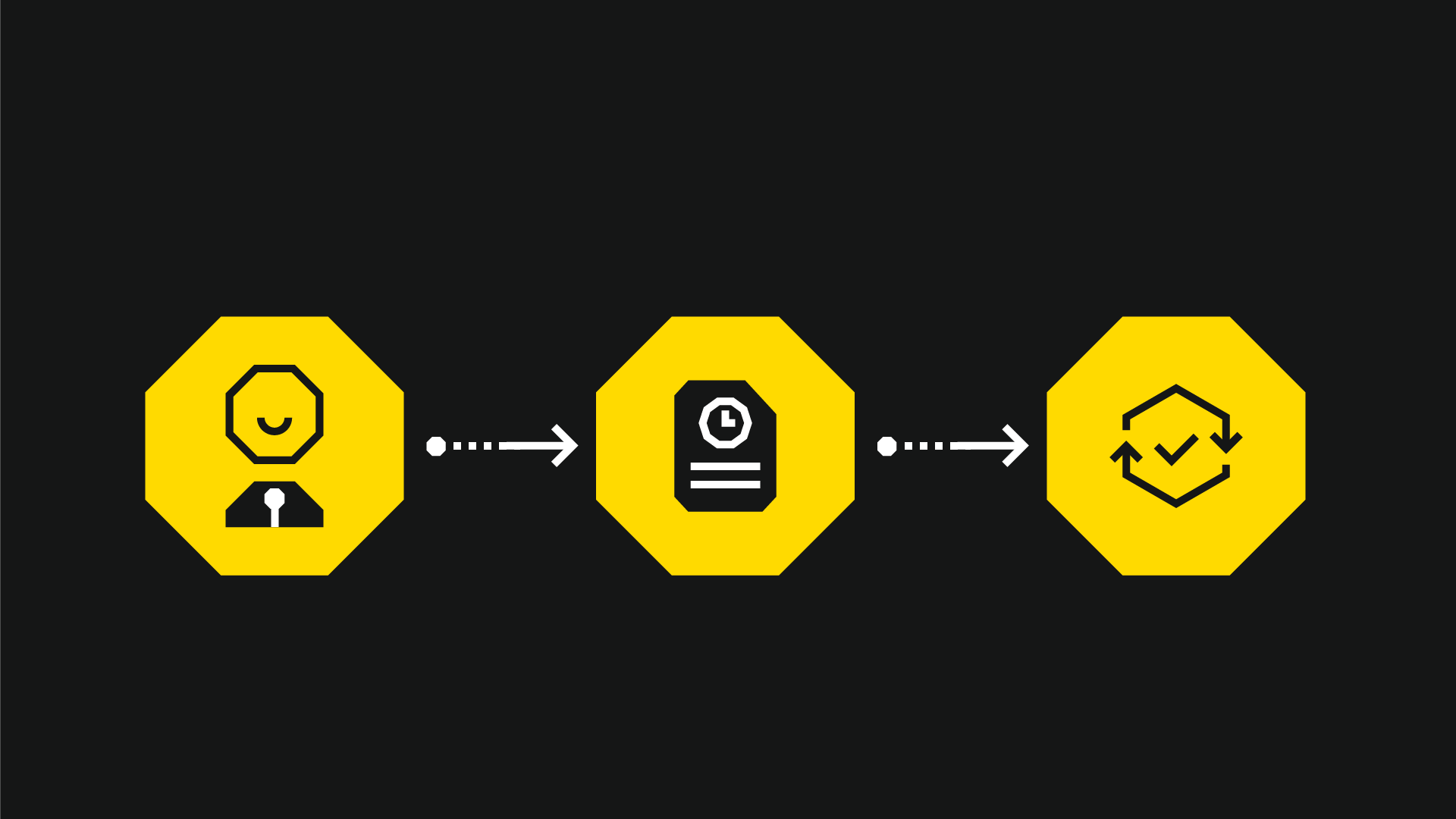
We recommend that organisations who want to invest in offensive security follow this rough progression:
→ Vulnerability scanning (and patching) → Pen testing → Red teaming
Getting value from a red team exercise requires an organisation to have a functional security operation centre (i.e., a SOC, SIEM framework).
An organisation that doesn’t have these things in place can still do a red team exercise, but it won't get nearly as much value out of it. That said, on some occasions, a red team exercise that uncovers critical findings can work as a driver for allocating security budget, as it accurately demonstrates the impact of a sophisticated, persistent attack targeted against the organisation.
Red teaming’s key goal is to assess your defensive posture, so ideally, you should have an experienced blue team with established detection and response processes.
Before red teaming, an organisation should ideally gain assurances around its relevant security controls. Endpoint detection and response, malware resilience testing, and phishing exercises can help ensure that telemetry, detection and prevention capabilities are of a good standard.
This way, the centralisation of the aforementioned logs, as well as the defensive team's monitoring and response performance, will be better assessed during the red team engagement.
Since they've reviewed individual security controls, the organisation will also be better prepared and increase its likelihood of defending against the red team (or a real attack).
A purple teaming exercise, where a red and blue team collaborate openly, is also a good way to prepare for a red teaming exercise.
Red Teaming Versus Pen Testing Scope
Another way to think about the difference between pen testing and red teaming is scope.
Red teaming assesses defences, whereas pen testing focuses more on the assets themselves.
Pen testing has a narrow, specific scope (usually testing a specific asset or group of assets) and no mandate to avoid detection.
Red teaming has a wide scope - often the entire organisation - and is designed to avoid detection for as long as it makes sense.
SECFORCE’s preferred approach to red teaming is to show clients different thresholds at which they are able or unable to detect an attack.
We think a red team should be as stealthy as possible, but if an attack seems to go totally unnoticed, red teamers should intentionally increase the "noise" they make to see whether detection happens.
For example, if a red team hasn't been detected during the whole engagement, on the last day, with the organisation’s permission, we might add a high-privilege user to see if this incredibly loud activity would be detected.
Often, this added noise is still missed, but the client has the advantage of being able to see the different levels at which their security posture needs improvement.
Talk to Offensive Security Experts
Name an offensive security test type or methodology, and we are likely to have expertise in it.
SECFORCE is a CREST-certified pen testing firm and qualified to deliver best-in-class red teaming.
We pride ourselves in turning our team's decades of experience into easy-to-follow advice on offensive security.
Whether you're considering a pen test or looking to do a red teaming exercise, we would love to talk to you and answer any questions about offensive security.
Some of the world’s leading organisations continue to trust SECFORCE to test their systems because they have seen us excel in complex environments with variable conditions. Our experienced and accredited testers are committed to delivering professional, ethical, and value-driven red teaming engagements.
Contact us today.