Many penetration testers rely on unicornscan’s speed to perform UDP portscans. Sometimes, a first pass is made with unicornscan to detect open UDP ports and then a second pass is made with nmap on those ports to find additional information about the service.
In a recent penetration test we came across an interesting situation where nmap could detect an SNMP service running on the target but unicornscan missed it.
To understand what was happening we wiresharked both scans and compared the packets sent by both scanners.
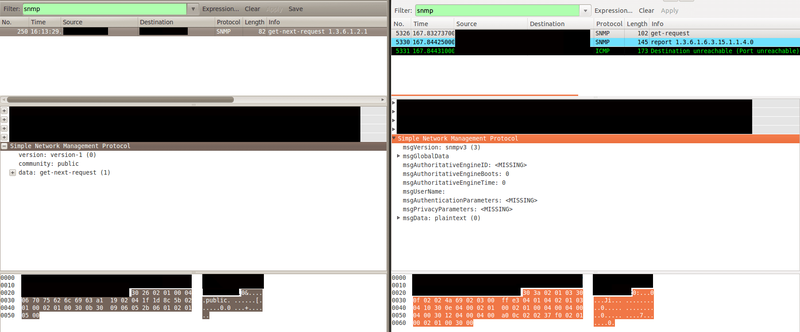
On the left we see the packet sent by unicornscan and on the right the one sent by nmap.
What had happened was that the service running was SNMPv3 and while nmap was sending an SNMPv3 get-request, unicornscan was sending an SNMPv1 get-request which was’t understood/supported by the remote service.
Fortunately, unicornscan is a flexible tool which allows the creation of custom payloads. Creating a payload is as simple as adding the new payload to the configuration file (payloads.conf). By inspecting this file we saw that, as expected, there was an SNMPv1 payload which corresponded exactly to the bytes we saw in wireshark (see selected bytes).
Following this logic, all we had to do was create a payload from the bytes selected in the second capture file. Thus, the new payload looks like this: