Whilst in the web application development world it is becoming very well understood that “you should never trust the data from the client side”, this is not always the case in local applications.
In web environments any restriction enforced at the client side can be easily bypassed with the use of a web proxy. However, security mechanisms enforced in desktop applications sometimes can be manipulated to perform unauthorised actions.
During a recent penetration test we found a desktop application which needed to be assessed in regard to security. GUI manipulation was used to conduct a number of attacks.
The tool of choice for this particular attack was “DARKER’s Enabler“:
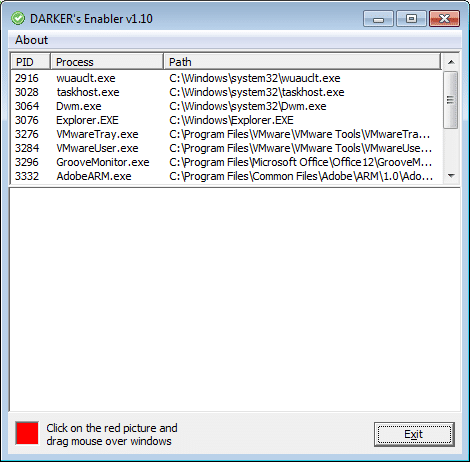
DARKER’s enabler is a tool which allows showing and enabling objects in Windows applications.
The application to be tested had a number of disabled fields that required to be modified for the purpose of the penetration test. Specifically the “Encrypt” checkbox needed to be unchecked, however the application showed the field disabled:
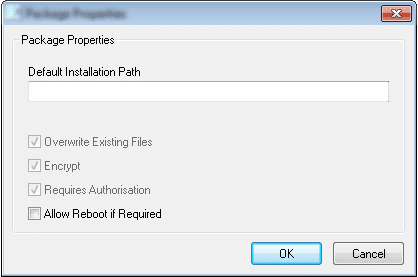
With Denabler we dragged-and-dropped the red square to the target application in order to identify de Windows handler of the field and then enabled it:
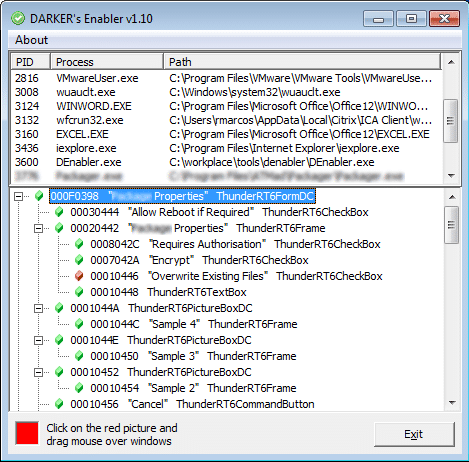
The action enabled the field and allowed the penetration testers to disable the encryption in the application, which resulted vital in the outcome of the penetration test:
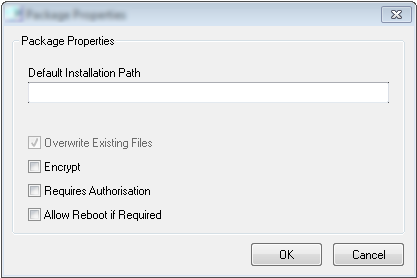
As shown above, GUI manipulation can lead to unwanted consequences. Extra caution needs to be exercised during the planning and development process to minimize the risk of GUI manipulation.