Which Cybersecurity Framework to Choose (and When): A Real Comparison of Cyber Frameworks
Published on Feb. 16, 2026 by SECFORCE
“Good cybersecurity programs are all alike, but bad programs are always bad in their own unique way.”
In our decade-plus of cybersecurity consulting experience, the good cybersecurity programs we encounter all use cybersecurity frameworks.
But what exactly is a cybersecurity framework?
We asked our team of cybersecurity consultants, including Nikos Vassakis.
According to our team (who have over 100 years of combined cybersecurity experience), a cybersecurity framework is voluntary guidance that gives you a template for “doing security right.”
Using a framework also signals to customers, investors, and partners that you take security seriously.
Following a cybersecurity framework gives you a checklist of processes, capabilities and technologies that give you assured risk reduction.
If you lead, work for, or invest in a company that’s still early in its IT journey (or are considering following a cybersecurity framework for other reasons), then the rest of this article should help you understand the what, why, and when of cybersecurity frameworks at a high level.
SECFORCE helps companies like yours implement cybersecurity frameworks. Contact us for a free discovery call.
3 Ways to Know You Need a Cybersecurity Framework
Any organisation with IT systems or data worth protecting will benefit from following a formal cybersecurity framework. That’s universally true.
But there are certain times in a company’s lifespan when choosing and sticking to a cybersecurity framework goes from being a “nice-to-have” to an urgent necessity.
Recognising these moments ahead of time is a real business advantage. It helps you avoid the stress, cost, and risk associated with rushing a framework implementation at the last minute.
Here are some of the situations where your business will almost certainly need a cybersecurity framework.
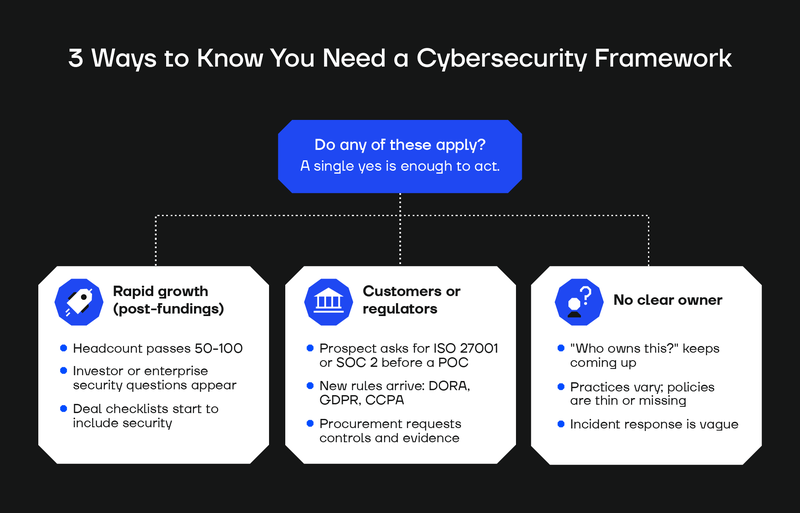
Rapid business growth (often after funding)
Informal cybersecurity habits typically start to break down when a company exceeds 50 to 100 employees. That’s also often the same point when threat actors begin paying closer attention.
Typically, as a seed or early-stage startup shifts toward an established business (or a Series A+ funding round closes), cybersecurity-related questions are going to arise from potential future investors and enterprise clients. At this point, security due diligence also tends to appear on deal checklists.
This is exactly when an organisation needs to rapidly evolve from having developers “think about security” to assigning people to dedicated roles and having some kind of overarching strategy for cybersecurity. In other words, this is exactly when a framework becomes non-optional.
Your customers (or regulators) become interested in your cybersecurity
With growth comes a new set of external pressures.
Some businesses feel these pressures almost immediately after they emerge from stealth, enter a new market, or start scaling up sales to target enterprise customers or customers in regulated industries.
For example, a prospect might ask directly for security framework details (like ISO 27001 certification) before signing a service agreement or deploying a POC of your solution.
In other cases, your industry might introduce new rules, such as the Digital Operational Resilience Act (DORA) in the financial sector, or you may start to come into contact with regional mandates (like the California Consumer Privacy Act or the General Data Protection Regulation), which carry real penalties for non-compliance.
In these scenarios, adopting a cybersecurity framework helps you meet the expectations of customers, partners, and regulators.
No one currently owns cybersecurity (or it's informal)
One of the strongest internal signals that it’s time for a cybersecurity framework is when the question “Who is the owner of this?” arises, whether in board meetings, management discussions, or within IT team conversations.
Sometimes, an audit reveals the same problem: security practices vary by team, policies are thin/undocumented/not approved or communicated to people involved, incident response plans are unclear, and nobody owns the program end‑to‑end.
Unfortunately, many organisations only realise this is a problem after a cybersecurity incident occurs. As we explain in another blog post, it’s much better to know and address these issues ahead of time.
Every major cybersecurity framework provides a structured way to solve this problem by defining clear roles, responsibilities, and accountability across the organisation.
Which Cybersecurity Framework Do You Need? Comparing Common Frameworks
Typically, the growth stage companies we talk to are choosing between one of three cybersecurity frameworks: CIS Critical Security Controls (CIS Controls), ISO 27001, and Secure Controls Framework (SCF).
But which one should you choose?
A quick rule of thumb: Pick CIS Controls for immediate hardening, ISO 27001 for market credibility through certification, and Secure Controls Framework (SCF) for a broad, strategic blueprint.
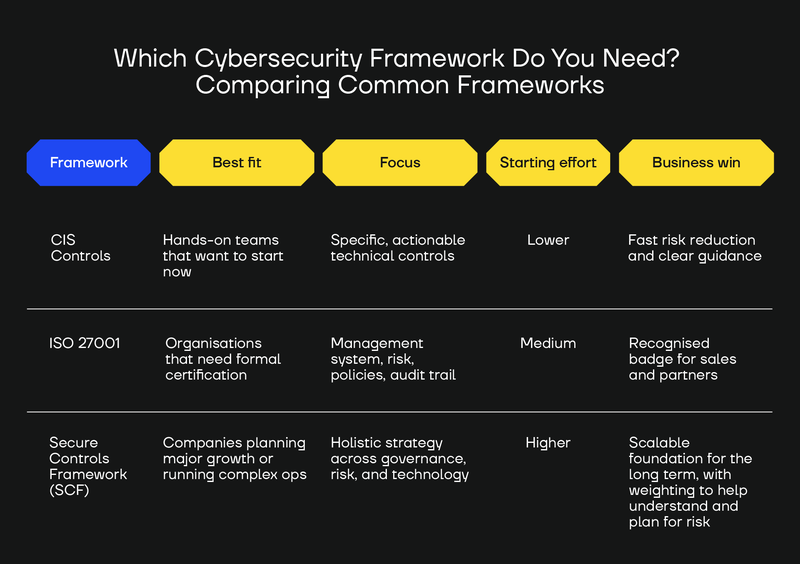
Technical-first approach? CIS Critical Security Controls
CIS Critical Security Controls (CIS Controls) are for when your technical team wants to get hands‑on and start hardening systems right away.
The guidance is a series of 18 concrete best practices. They are immediately usable: inventory what you have, lock down endpoints and accounts, apply patching and logging that you can verify, and then expand.
The maturity bar is low, so progress shows up quickly. The business gain is simple: measurable risk reduction in weeks, guided by a clear, practical checklist.
There is no external audit or certification.
- Best for: Technical teams wanting hands-on security implementation that need to start doing security.
- Focus: Specific, actionable technical controls that can be implemented immediately.
- Maturity requirement: Lower - can start implementing right away. No audit requirement.
- Business benefit: Immediate security improvements with practical technical guidance.
Certification-driven? ISO 27001
Choose ISO 27001 when clients, partners, or the market ask for a recognised badge.
ISO 27001 is probably the best-known cybersecurity standard in the world and defines a full information security management system with risk assessment, policies, roles, training, and internal audits.
It also involves a certification audit by an accredited body.
ISO27001 takes real organisational commitment and documented processes, so the effort sits in the middle of the spectrum. The payoff is being able to engage in procurement processes and give reliable assurance to stakeholders who need solid proof.
- Best for: Formal certification for clients, partners, or competitive advantage.
- Focus: Comprehensive management system with audit trail and formal certification.
- Maturity requirement: Medium in the sense that it requires documented processes and organisational commitment. Audit required.
- Business benefit: Market credibility, competitive advantage, and customer assurance through formal certification.
Comprehensive strategy for a complex organisation? Secure Controls Framework (SCF)
Secure Controls Framework (SCF) is a very comprehensive meta framework with over 800 controls that map onto all existing data privacy laws, regulations, and frameworks.
It’s designed to provide organisations with the flexibility to comply with various standards and/or frameworks (e.g., those subject to more than two separate regulations, or those running complex businesses or multiple organisations within the same group), thereby necessitating a broad strategy that encompasses governance, risk, and technical practices.
It organises cybersecurity work into 33 domains, each mapped out with a different three-letter acronym. These are really comprehensive and include everything from Artificial Intelligence (AAT) to Endpoint Security (END).
In our experience (and according to their own governing council), the SCF asks for deep cross‑functional alignment and considerable resources to use properly. As a result, the maturity bar to implementing it fully is higher compared to other frameworks in this article.
According to the SCF council itself, the framework is likely to be “overkill” for companies with only 1 or 2 compliance requirements. However, for organisations aiming to remain agile and fully prepared for future regulatory changes or the introduction of new standards, adopting the SCF can be a strategic advantage that provides a scalable, future-proof foundation that supports long-term compliance and risk management goals.
However, the benefit is a scalable foundation that supports enterprise‑level operations without losing sight of day‑to‑day controls.
Note that SCF does not involve an external audit but does include a self-assessment toolkit for objective analysis.
- Best for: Planning significant growth or managing complex operations, even across multiple jurisdictions, as SCF facilitates mapping your current SCF standard to virtually any regulatory requirement.
- Focus: Holistic approach covering governance, risk management, and technical controls.
- Maturity requirement: Higher because it requires substantial organisational commitment and resources.
- Business benefit: Scalable foundation for enterprise-level security that covers both technical and management aspects.
What Happens If You Don't Implement Security Frameworks?
Frameworks are to security programs what scaffolding is to a building site. Without a framework, any security program will be chaotic, informal, and liable to stop working at an unexpected moment.
Our experience is that organisations without proper security frameworks face increased vulnerability to cyber attacks and data breaches. They also struggle to meet client security requirements, meet evolving regulatory requirements (remember: it’s not just today’s regulations that will impact your business), and respond effectively when incidents happen.
It’s our strong opinion that forgoing a cybersecurity framework is a mistake. Don’t wait until you experience a cybersecurity incident to realise you needed one.
Scale Your Security Program
Pick the right framework, plan the rollout, and get it working across your teams with SECFORCE.
Our team will guide you through framework selection and implementation, translating generic requirements into actions that fit your tech stack, risk profile, and industry.
We give you long‑term strategic guidance tuned to your goals. Our focus is on delivering lasting security value, which includes tested controls, clear ownership, and evidence that can be shown to customers and auditors.
Contact us for a short discovery call.
Cybersecurity Security Framework FAQs
We receive numerous questions from potential clients regarding cybersecurity frameworks. We’ve listed some of the most common ones below.
If I choose one framework, do I need to stick with it?
Not at all. The best practices outlined in any framework provide a solid foundation, and improvements you make are generally transferable across frameworks.
This means that if you decide to switch frameworks or if your regulatory compliance requirements change, your prior efforts won’t be wasted.
Do I need to implement the entire cybersecurity framework?
Ideally, yes, but in practice, no. Very few organisations fully implement every aspect of any given framework.
Even with the best intentions, companies have varying security maturity levels across different processes. For example, an organisation might be very good in one area but lacking in others.
Conducting a gap analysis and maturity assessment helps identify strengths and highlight areas needing improvement, so organisations can prioritise and focus their efforts effectively.
Should I try to achieve “ultimate maturity” when implementing a new cybersecurity process or function?
No, there’s no final goal when it comes to cybersecurity maturity. Most frameworks are designed in “levels,” and it’s best to manage expectations by progressing gradually.
Focus on moving from one level to the next (e.g., Level 1 to Level 2, then to Level 3), rather than aiming for the highest possible level right away. This helps prevent the process from becoming overwhelming.
For most organisations, reaching Level 3 provides strong security. Levels 4 and 5 are mostly enterprise territory (meaning that the cost of implementation often overshadows the benefits).
You may also be interested in...
We’ve tested thousands of web applications over almost two decades… and we can confirm that a large percentage of web application exploitation vectors can only be discovered through penetration testing.
See more
Our deep dive into what is Gold Teaming, how to prepare for one and why it's getting more and more important within mature organisations.
See more