We've been helping companies assess and upgrade their penetration testing capabilities for over a decade.
Based on that experience, we want to share our thoughts on why it's better to do more frequent pen testing than you likely do at present.
TL;DR: Generally, penetration testing benefits (resilience, cost, and compliance) improve as your penetration testing program becomes more mature and frequent.
In the rest of this article, we will dive into exactly why pen testing more often is better than less often, plus what penetration testing maturity actually means for your organisation.
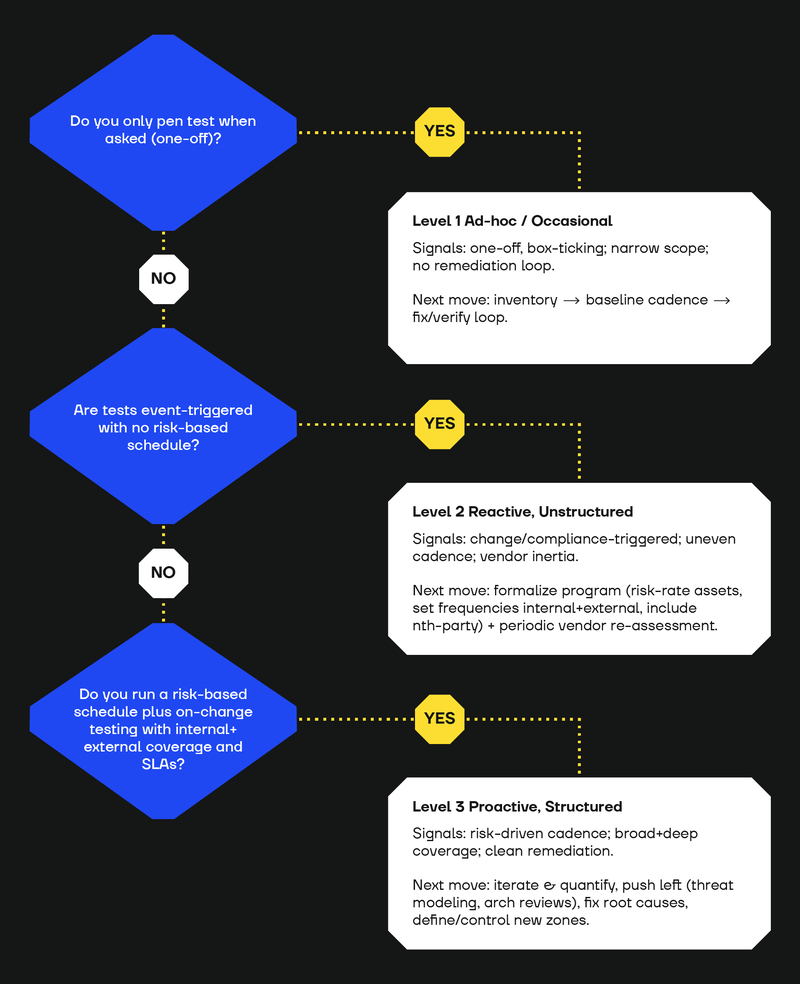
How to Assess Your Penetration Testing Maturity At a Glance
Use the following table to quickly identify where your current approach to penetration testing stands and what steps you should take to level up.
Companies Tend to Fall Into 2 Broad Categories of Pen Testing Maturity
There are many reasons why one company might be more mature and another less so when it comes to penetration testing.
Budget is a core reason why some companies are more mature than others. But different levels of penetration testing maturity can also come as a result of:
- Security culture.
- Risk awareness.
- Technical knowledge about what pen testing can and cannot do.
Here’s how to understand your level of penetration testing maturity and what that means for your cybersecurity posture.
Less mature companies test reactively
You could describe this kind of company’s approach to testing as "response-driven.”
For response-driven organisations, pen testing happens as a means to an end or a way to tick a box.
We’ve seen two subcategories of reactive companies, one slightly more mature than the other:
Occasional and ad hoc (lowest penetration testing maturity level)
This is the least mature approach to pen testing.
Testing only occurs because someone (usually a client) requests a penetration test report, or there is a specific (externally driven) reason.
Many smaller companies are at this level of penetration testing maturity.
These are companies that may need to provide a client with a penetration test report for procurement purposes, and that test will likely be a one-off exercise. The next time they conduct a penetration test will be when they receive another request or when the previous one is considered “expired” by the requester.
Or, testing might not happen at all, leaving the company highly exposed to potential unknown risks. We have also seen some companies at this level confuse pen testing with vulnerability scanning.
Companies with ad hoc testing programs usually:
More frequent but unstructured (slightly more mature penetration testing)
These are companies that conduct penetration tests more regularly but still treat penetration testing as something to be done in response to a specific event, such as making major internal or external IT changes or updating a product/application.
Other triggers for organisations at this level of penetration testing maturity to pen test might include:
- Specific compliance requirements (e.g., annual testing of an application).
- Similar businesses being hacked.
- Big shifts in operations/IT environment structure.
- Management concerns about a particular cyber risk (e.g., Log4j).
- When a wider security assessment includes a pen test.
Penetration testing for these kinds of organisations tends to be unstructured in terms of when it occurs and may not integrate into a broader security program.
Learn how cybersecurity consulting can be a secret weapon for a great pen test.
Security and IT teams here tend to be wary of pen testing as they know that unexpected results can catch them off guard. Consequently, they may try to steer testing toward expected results. For example, they might use the same vendor year on year with the "expectation" that results will always be similar.
More mature companies ensure they are receiving best-in-class service through a process of regular capability reassessment.
Some organisations periodically conduct structured exercises or mock assessments to compare vendors’ capabilities and ensure they continue to meet expectations.
This approach helps maintain strong coverage and high-quality outcomes without unnecessarily disrupting long-term relationships or incurring additional procurement overhead.
High penetration testing maturity companies test proactively
At the higher levels of penetration testing maturity, organisations have a structured program.
Penetration tests occur as part of a security improvement program; everyone is aware of what to expect, and a plan is in place to address the results.
A company with a mature pen testing program has some or all of these three features:
In-depth testing that happens regularly
The primary difference between a mature and immature program is that penetration testing will occur because a company wants to invest in building its resilience. (Note: Mature organisations will still do pen testing due to “push factors,” e.g., compliance or major changes to applications or their environment).
Testing to build resilience means:
a) Testing critical systems at frequent intervals.
b) Testing less obviously at-risk parts of the environment, i.e., parts of their systems that might seem unlikely to be accidentally exposed online, but would still lead to significant disruption if they were hacked.
In a mature organisation, the testing timeline is typically managed through a structured penetration testing programme, which involves maintaining a clear asset inventory and defining a testing frequency for each asset.
Learn how often should you pen test.
Organisations with a mature programme also assess not only external threats (“outside-in”) but risks originating within the perimeter, such as potential internal attackers or disgruntled employees.
A penetration testing governance structure
There is a penetration testing governance structure that is regularly reviewed and updated to ensure its effectiveness and relevance.
The benefit of a governance structure is that a company gains the ability to properly define the scope of penetration testing. A structured approach to planning what should be tested, how, and when saves time and money.
This means the company knows how to apply the right security test for the right purpose. It conducts frequent vulnerability assessments to maintain broad security hygiene and complements them with targeted penetration tests at a frequency determined by the criticality of the asset, its exposure, and other relevant factors.
Connection between security and the rest of the organisation
At higher levels of maturity, companies tend to integrate security into their core business operations.
This can involve considering security early in the development process for any application, including defining security requirements, performing threat modelling, and conducting architecture reviews, in addition to penetration testing.
It can also involve testing infrastructure early in a build or change so that security can be built in rather than “bolted on” to whatever service or system is launched.
What Penetration Testing Maturity “Feels Like”
The more mature a penetration testing program is, the easier, more effective, and more impactful testing (and the cybersecurity program as a whole) becomes.
A company with a mature pen testing program can unlock incredible security benefits compared to its peers. Benefits that security teams, CISOs, and non-technical managers will feel on a day-to-day basis.
These benefits include:
Cost Savings and Other Financial Benefits
- Potential cost savings on cybersecurity insurance, as lower risk profiles can lead to reduced premiums.
- Possible reduction in ICT costs in the long term.
- Ability to avoid fines and legal liabilities in case of incidents or litigation by demonstrating "reasonable" precautions. Board members love this.
- Ability to quantify a security program’s effectiveness and optimise it, leading to security becoming more cost-effective.
Improved Security Effectiveness
- Identifying more weaknesses more accurately.
- Assurance against threats that other organisations are terrified of and the ability to react quickly to new types of risks.
- Reduced likelihood of breaches and hacks. Pen testing will, by its nature, significantly minimise your breach risk if the issues identified during testing are properly mitigated.
- Better visibility. Although a pentest tends to stay within the scope, having a mature testing program will mean that even systems that have yet to be tested are accounted for.
- Early identification of security issues, which can solve root cause problems (like the development of insecure features) and avoid expensive remediation (or risky deployments) further on.
- Greater levels of confidence in the security of your IT environment.
- Establishment of a systematic approach to security requirements by integrating pen testing results, enabling the creation of secure baselines that all future applications must adhere to.
Reputation and Compliance
- A trustworthy reputation among customers, clients, and partners who know that trusting this business's application/API/service will not get them in trouble.
- Less stress about complying with legal and regulatory requirements (PCI/DSS, NERC, ISO 27001, etc.)
- The ability to confidently push ahead with IT configurations or service deployments that competitors might hold back on due to fear of unknown risks.
For CISOs, a mature testing program can unlock paths towards reducing cybersecurity risk.
For example, an experienced CISO in a company with high testing maturity will be able to read a penetration test report for various parts of their environment and identify the root causes of recurring risks.
They get to see exactly where they might need additional control zones. This can result in lightbulb moments, such as “Oh, what’s our backup segregation or partition strategy?”
Level Up Your Penetration Testing Maturity
SECFORCE pen testing experts have helped hundreds of organisations assess and improve their penetration testing maturity.
Contact us for a free consultation today to explore how you can develop a more mature security and testing program within your company or learn more about our penetration maturity assessment services.