DORA Microenterprise Requirements: Everything You Need to Know
Published on Jan. 20, 2026 by SECFORCE
Microenterprises are in scope of the Digital Operational Resilience Act (DORA), but they benefit from reduced requirements in many areas of DORA and are excluded altogether from others.
This is thanks to DORA’s “principle of proportionality.” DORA tries to avoid putting disproportionately high burdens on smaller entities while still ensuring a baseline of cyber maturity across the entire EU financial sector.
The rest of this blog post lists the (lighter touch) DORA requirements that apply to microenterprises. We also show you which requirements do not apply to microenterprises at all.
How Does DORA Define “Microenterprise”?
DORA defines a “microenterprise” as:
“A financial entity, other than a trading venue, a central counterparty, a trade repository or a central securities depository, which employs fewer than 10 persons and has an annual turnover and/or annual balance sheet total that does not exceed EUR 2 million.”
DORA’s Proportionality Principle
DORA tries to consider an organisation's size and management structure. Its authors know that smaller entities are likely to struggle to meet requirements designed for enterprises.
For example, in a 10-person IT team where 2-3 people are in management, it is impossible to keep ICT risk management independent of other roles. Smaller companies will have a lot more shared responsibilities than larger organisations.
The same goes for technology. A smaller organisation's technology stack is more concentrated. Critical functions will be harder to isolate from the rest of the environment. Comprehensive testing of critical functions effectively means testing everything in these cases.
That’s why DORA adopts the “principle of proportionality.”
So long as organisations cover DORA fundamentals at a level adequate for their particular risk profile, they can be DORA compliant.
For example, microenterprises are completely exempt from certain DORA requirements like advanced threat-led penetration testing (Article 26) and formal yearly internal ICT audits (Article 6(6)).
Where DORA exempts microenterprises from particular obligations, it usually does so by stating “financial entities, other than microenterprises, shall …” or by placing microenterprises (alongside certain other small entities) into a separate simplified framework (Article 16).
Ultimately, DORA (in some cases) is designed to protect small organisations from overly onerous security burdens while giving them the push needed to do better at securing their environments.
Microenterprises Are Excluded from The Following Requirements
The following DORA requirements do not apply to microenterprises.
Here’s a quick table summary (with more details below).
ICT risk management
Article 5. Governance and organisation
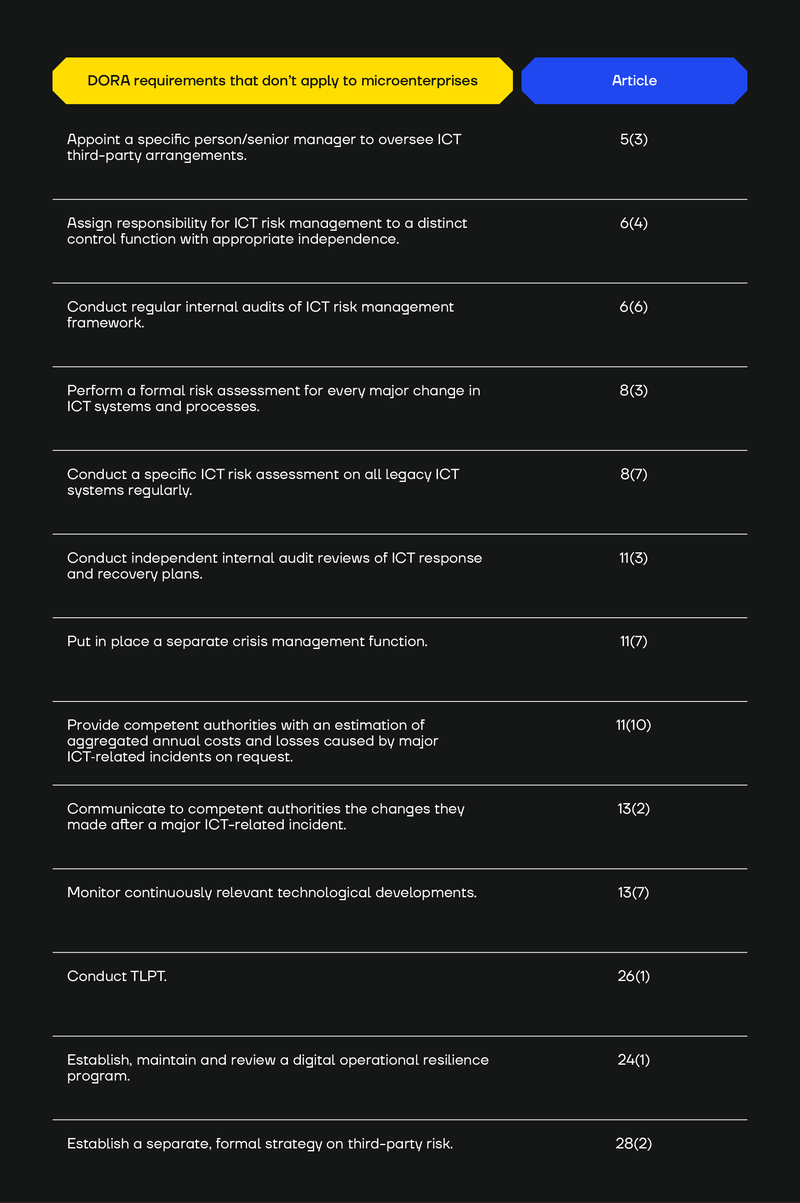
Microenterprises are exempt from the requirement of having someone in their organisation (or assigning a senior manager) to oversee ICT third-party arrangements, specifically to oversee the related risk exposure and relevant documentation. Article 5(3).
Article 6. ICT risk management framework
Microenterprises are exempt from the requirement to:
- Assign responsibility for ICT risk management to a distinct control function with appropriate independence. Article 6(4)
- Have the ICT risk management framework subject to a regular internal ICT audit. Article 6(6)
Article 8. Identification
Microenterprises are not required to:
- Do a formal risk assessment for every major change to their ICT systems and processes (though they should still keep ICT risks under review in a proportionate manner). Article 8(3).
- Conduct a specific ICT risk assessment on all legacy ICT systems regularly and at least yearly (and before and after connecting technologies, applications, or systems). Article 8(7).
Article 11. Response and recovery
Microenterprises:
- Are not subject to independent internal audit reviews of ICT response and recovery plans implemented as part of ICT risk management framework. Article 11(3).
- Are not required to have a separate crisis management function. Article 11(7)
- Need not provide competent authorities with an estimation of aggregated annual costs and losses caused by major ICT‐related incidents on request. Article 11(10).
Article 13. Learning and evolving
All financial entities (including microenterprises) must conduct post‐incident reviews whenever a major ICT‐related incident disrupts their core activities. However, microenterprises are not required to communicate the changes they have implemented following such a post‐incident review to competent authorities Article 13(2).
Microenterprises are not required to continuously monitor relevant technological developments. Article 13(7).
Digital operational resilience testing
Article 24. General requirements for the performance of digital operational resilience testing
Microenterprises do not have to establish, maintain and review a digital operational resilience testing program. Article 24 (1).
Article 26. Advanced testing of ICT tools, systems and processes based on TLPT
Microenterprises are exempt from advanced threat-led penetration testing (TLPT). Article 26(1).
Managing of ICT third-party risk
Article 28. General principles
Microenterprises are exempt from establishing a separate, formal strategy on third-party risk. Article 28(2).
Reduced Requirements for Microenterprises
The following DORA requirements are reduced for microenterprises.
Here’s a quick table summary (with more details below).
ICT risk management
Article 6. ICT risk management framework
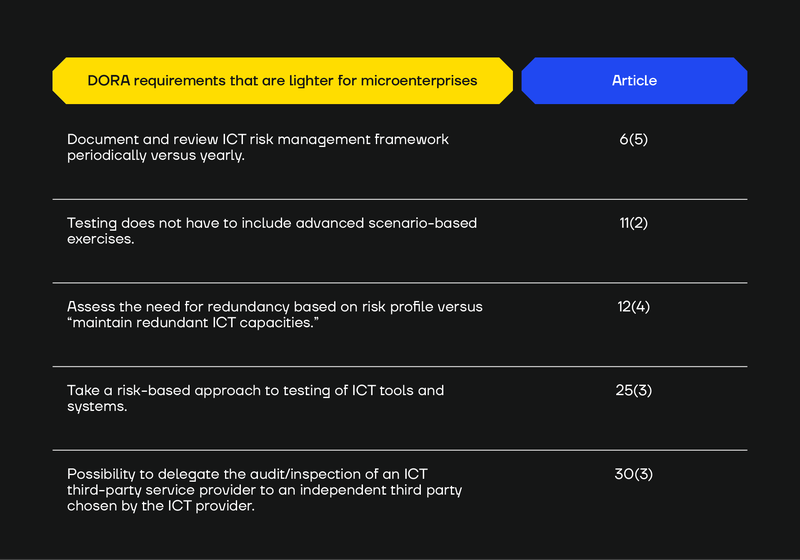
Whereas financial entities must document and review their ICT risk management framework at least once a year, microenterprises may do so only “periodically,” reflecting lower complexity and fewer resources.
However, like financial institutions, microenterprises must review their framework after a major ICT-related incident and following supervisory instructions or conclusions derived from relevant testing or audit processes. Article 6(5)
Article 11. Response and recovery
All financial entities, including microenterprises, must perform some testing (namely, an annual test of continuity/response/recovery plans) in line with the overall proportionate approach under DORA.
However, microenterprises do not have to expand the testing to include advanced scenario-based exercises (e.g. cyber-attack scenarios, testing switchover from primary to backup ICT systems, etc.). Article 11(2)
Article 12. Backup policies and procedures, restoration, and recovery procedures and methods
Non‐micro entities “shall maintain redundant ICT capacities,” whereas microenterprises only have to assess the need for redundancy based on their risk profile. Article 12(4)
Digital operational resilience testing
Article 25. Testing of ICT tools and systems
Like financial entities, microenterprises also have to test their ICT systems, but they can do so using a simpler, “risk‐based” strategy and accounting for the limited staff and resources they may have.
They can pick which tests to do (e.g., vulnerability assessments and scans, physical security reviews, penetration testing, etc.) based on the urgency, risk type, and importance of their systems or data.
Essentially, microenterprises don’t need the same breadth of testing as larger financial entities as long as they remain proportionate to their scale and risk levels. Article 25(3).
Managing ICT third-party risk
Article 30. Key contractual provisions
Financial entities normally have a direct right to audit and inspect an ICT third‐party service provider. But microenterprises can delegate that audit/inspection right to an independent third party (chosen by the ICT provider). Even with that arrangement, the microenterprise can always ask the third party for any information or assurances it needs about the ICT provider’s performance. Article 3(3)
Need Help Complying with DORA? SECFORCE Can Help
Whether you’re a micro-entity or another organisation that needs help with DORA compliance, talk to us. We’re a DORA consultancy firm with vast experience helping financial service entities and businesses navigate complex compliance journeys.
Contact us today to learn more.
You may also be interested in...
When is an organisation ready for purple team testing? Have a look at the exact situations where purple teaming will deliver the most value, purple team testing timelines, and what happens after a purple teaming exercise is done.
See more
It’s not as simple as “just fixing things". This article is our advice on how to go from pen test results (and recommendations) to successful post-test remediation.
See more